Security

In the old days we had stand alone computers.. no network, no internet. Not as much fun but impossible to hack unless you could get to the actual computer.
Now we have online shopping, online games and hackers! You have almost definitely seen movies which relate to security, whether it’s hacking or biometric retina scanners (see pic above). But do you know about all of the different security threats that now exist?
Or all the methods to prevent them? Read on for many examples.
Malware
This is a general term for malicious software used to hack into a computer system. There are several types. For a quick overview check the BBC Bitesize descriptions below.
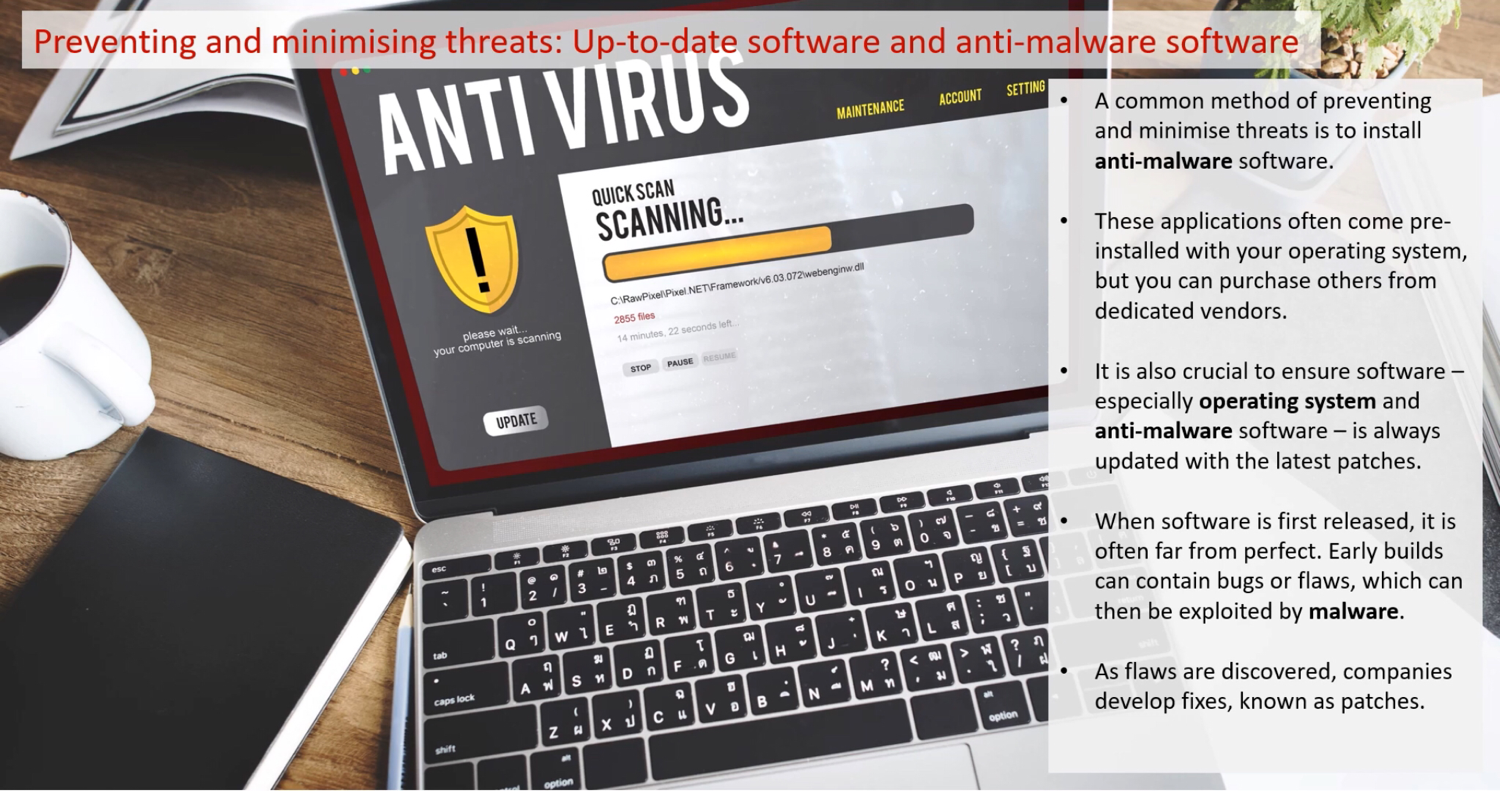
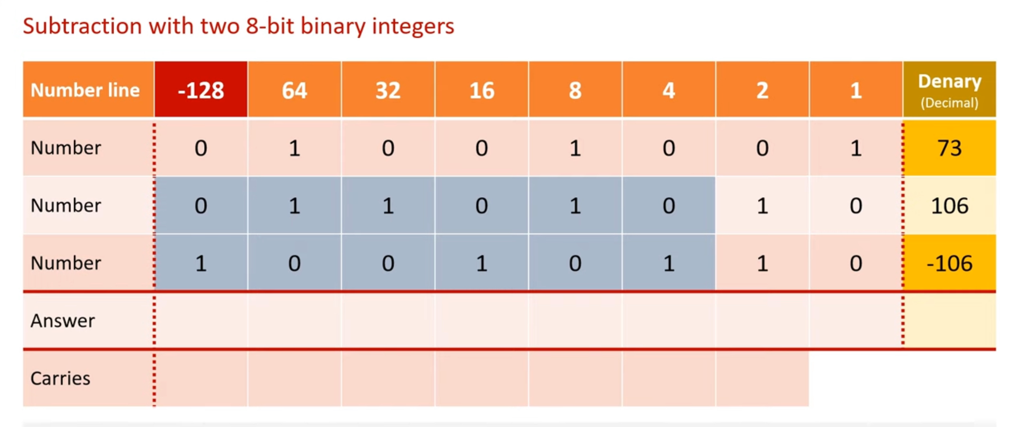
Phishing emails
This is a very common trick where emails are sent with the aim of getting you to login online so that your account details can be stolen. This type of scam works best if the email is from a financial organisation like a bank or payment company. Check the email here. There are several tricks that make it more likely to work:
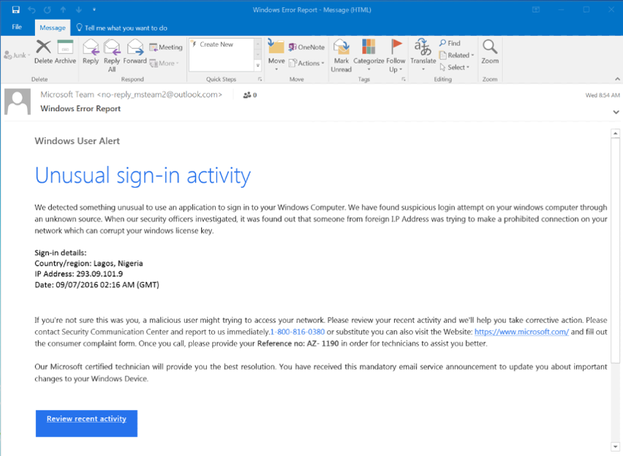
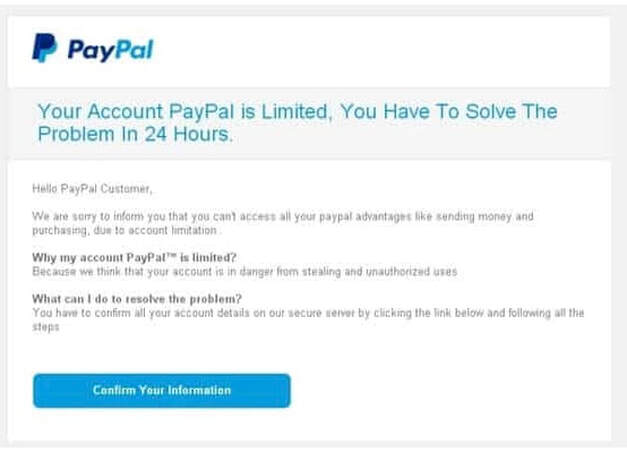
This type of phising email might work because:
- The email is apparently from a financial company.
- It has the company logo.
- It has a sense of urgency.. you only have 24 hours to solve the problem.
- It instills fear.. your account will be limited if you don’t act on this!
How do you spot a phishing email? Ask yourself these questions:
- Does it come from the company domain (e.g.PayPal.com)?
- Does the email contain spelling or grammar mistakes?
- Does the email address you in a general form (e.g. dear customer) rather than by your name?
Delivery companies phishing
It’s not just financial companies who need to worry about phishing, it’s almost any company. Click here for information from Hermes who deliver packages
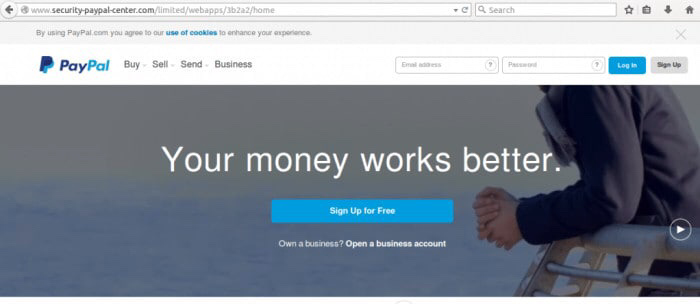
Pharming websites
If you click the login button you’ll be taken to a pharming website.
This website looks pretty realistic doesn’t it? It’s actually a really good pharming website. Great pharming websites look really official and are designed to get you to login. The hacker can then steal your login details, your financial details etc.
For a great website to find out more about PayPal scams click here.
It’s not all high tech: Shouldering
Shouldering (also known as Shoulder Surfing) is a type of social engineering technique used to get sensitive data such as pins and passwords by looking over the victims shoulder as they type or (less commonly) by listening out for keypresses and figuring out which key was pressed by the tone of the sound.

Brute Force
You could just guess? Does that seem like a dumb idea? Hackers actually do this. Sometimes on their own... sometimes by creating a program to help them. Brute force hacking software can find a single dictionary word password within one second! Don't think you're safe because your password isn't a single dictionary word, as these programs also often use lists of commonly used passwords, often obtained from data breaches.
Blagging
Someone you have just met asks you if you’ve ever had a pet, what was its name? Or they tell you their age and their birthday and ask for yours, Or you receive a phone call. The caller says they are from your bank checking for fraudulent activity. They ask you for your account details.


This is called blagging. How do you know? If in doubt never give out information to people that you don’t know. The bank will never ask for sensitive information over the phone.
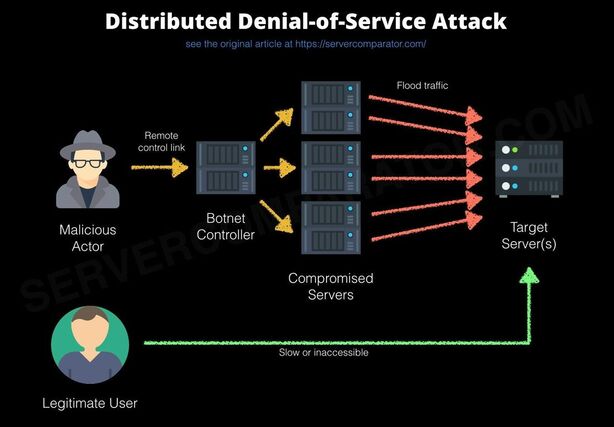
Denial of Service
A denial-of-service (DoS) attack is when an attacker makes it impossible for normal users to access computer systems or a network. Attackers flood with traffic the target web servers or networks. This means that they get overwhelmed and makes it difficult or impossible for anyone else to access them.

Many common DoS attacks are actually distributed attacks (DDoS), where the attack traffic comes from multiple places. This makes DDoS attacks far more difficult to detect and defend against than other forms of DoS attacks.
SQL Injection
SQL is the programming language used with databases. Expert hackers can create SQL which may look innocent but is actually designed to do something harmful. Find out more here.
Preventing Security Threats
We have seen that there is a lot of risk involved in sharing your sensitive data online. But there are also many ways to keep your sensitive data safe online. Click here and watch the video below to find out more.
Pen Testing
A penetration test, also known as a pen test or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system.
Firewalls
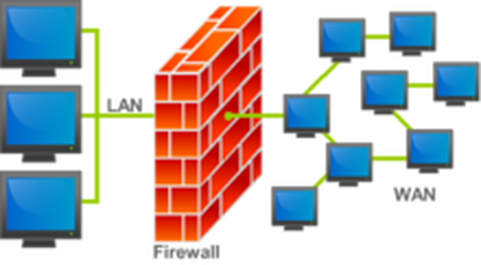
As the name suggests firewalls provide a barrier between a network and the hacker by monitoring all network traffic coming in and out of the network.
Finger print and face recognition
Fingerprint recognition works by using a light sensor to check the little ridges in each of our fingers which form a unique pattern.
Facial recognition works by using a photo to map out facial features and then comparing these when a person's face is scanned.


Two-factor authentication
Administrators can require two-step authentication and install an intrusion detection system that detects brute force attacks. This requires users to follow-up a login attempt with a second factor, like a physical USB key or fingerprint biometrics scan.
Want to know more?
Check the Kaspersky website if you want advice from a specialist security company by clickng here.
For an excellent website covering this topic click here. For great advice click here.